December 2023 Web Server Survey
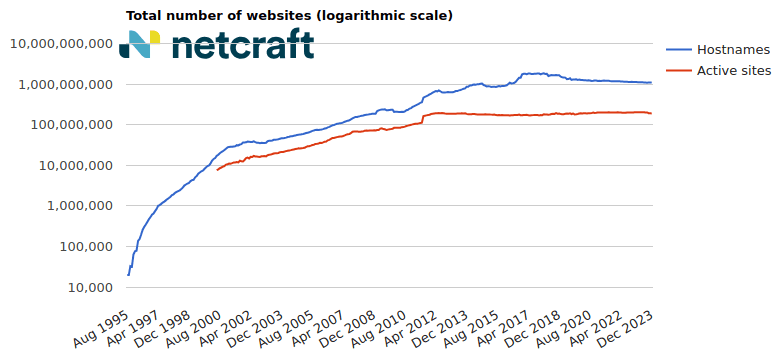
In the December 2023 survey we received responses from 1,088,057,023 sites across 269,268,434 domains and 12,355,610 web-facing computers. This reflects a loss of 4.1 million sites, an increase of 238,593 domains, and a loss of 128,028 web-facing computers.
nginx experienced the largest loss of 4.5 million sites (-1.79%) this month, and now accounts for 22.5% of sites seen by Netcraft. Microsoft suffered the next largest loss, down by 2.5 million sites (-9.65%).
OpenResty remains the largest growing vendor, gaining 3.3 million sites (+3.64%) and increasing its market share to 8.71%. Second to OpenResty is Google, which gained 1.5 million sites (+2.65%).
Vendor news
- Apache Tomcat versions 9.0.83, 10.1.16, 11.0.0-M14, and 8.5.96 were released.
- OpenResty version 1.21.4.3 was released, patching a bug that made it vulnerable to HTTP/2 rapid reset attacks.
- AWS held its annual re:Invent conference, with announcements including:
- Amazon Q – an AI assistant for businesses
- Amazon Aurora Limitless Database – a distributed database that can scale to manage petabytes of data
- R8g – a new memory-optimized and energy-efficient EC2 instance
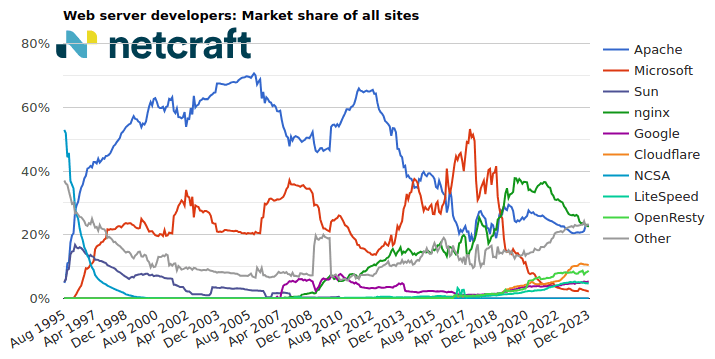
| Developer | November 2023 | Percent | December 2023 | Percent | Change |
|---|---|---|---|---|---|
| Apache | 248,343,154 | 22.74% | 248,118,087 | 22.80% | 0.06 |
| nginx | 249,368,944 | 22.83% | 244,903,710 | 22.51% | -0.32 |
| Cloudflare | 115,937,937 | 10.62% | 113,499,479 | 10.43% | -0.18 |
| OpenResty | 91,405,835 | 8.37% | 94,737,403 | 8.71% | 0.34 |
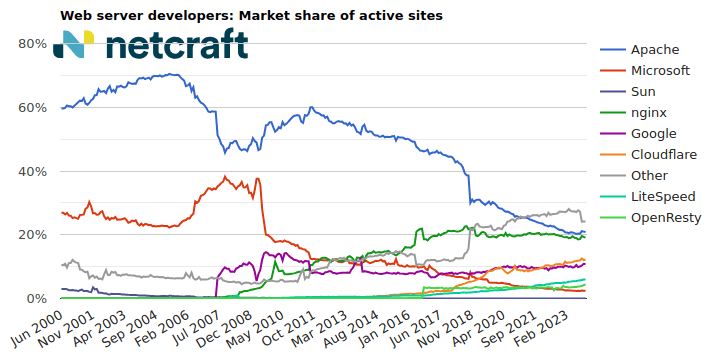
| Developer | November 2023 | Percent | December 2023 | Percent | Change |
|---|---|---|---|---|---|
| Apache | 40,080,759 | 20.98% | 39,476,338 | 20.84% | -0.14 |
| nginx | 36,927,632 | 19.33% | 36,176,461 | 19.10% | -0.23 |
| Cloudflare | 23,035,498 | 12.06% | 23,076,699 | 12.18% | 0.12 |
| 20,759,419 | 10.87% | 20,543,756 | 10.85% | -0.02 |
For more information see Active Sites.
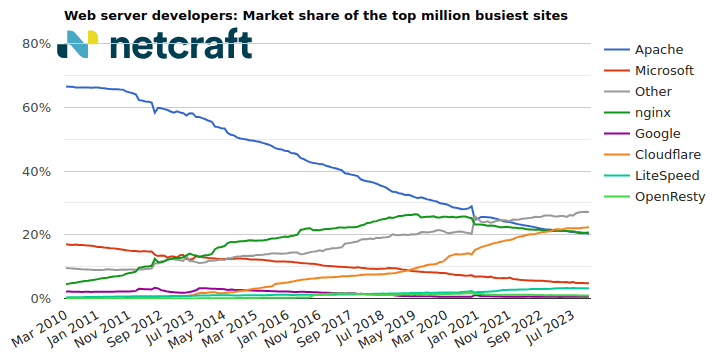
| Developer | November 2023 | Percent | December 2023 | Percent | Change |
|---|---|---|---|---|---|
| Cloudflare | 222,400 | 22.24% | 223,795 | 22.38% | 0.14 |
| nginx | 206,286 | 20.63% | 207,158 | 20.72% | 0.09 |
| Apache | 204,504 | 20.45% | 203,097 | 20.31% | -0.14 |
| Microsoft | 48,019 | 4.80% | 47,476 | 4.75% | -0.05 |
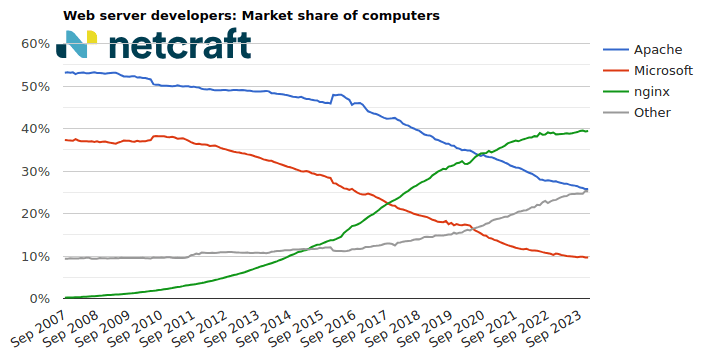
| Developer | November 2023 | Percent | December 2023 | Percent | Change |
|---|---|---|---|---|---|
| nginx | 4,904,964 | 39.29% | 4,867,232 | 39.39% | 0.10 |
| Apache | 3,212,874 | 25.74% | 3,183,227 | 25.76% | 0.03 |
| Microsoft | 1,205,605 |
…